Lessons From Fort Knox: How to Harden Your Enterprise Security & Cybersecurity
Explore the security concepts demonstrated by the nation’s most secure facility to learn how to harden your enterprise’s IT ecosystem
Fort Knox’s Vault is synonymous with security. Built between 1935 and 1936, the Fort Knox Bullion Depository at Fort Knox, as it’s actually known, was constructed using “16,000 cubic feet of granite; 4,200 cubic yards of concrete; 750 tons of reinforcing steel; and 670 tons of structural steel.” Simply put, it’s a building that the world’s top criminals can only dream of infiltrating.
However, most cybercriminals often aren’t striving to break into the U.S. Treasury’s top-secret facility. Rather, they’re looking for more realistic targets that will allow them to “make bank” with the least effort. These targets include companies like yours or your competitors by exploiting vulnerabilities within your environment.
Your data is your gold bullion. This is why enterprise security and cybersecurity are crucial to prevent corporations from becoming the next juicy target for cybercriminals. We’ll explore some lessons learned from Fort Knox’s security and how they can translate to your organization.
Let’s hash it out.
How Fort Knox Earned Its Reputation as the World’s Most Secure Facility

People often think Fort Knox and the Fort Knox Bullion Depository are the same. That’s not quite accurate, though. Fort Knox itself is a sprawling 109,000-acre multifunctional military installation in Kentucky with more than 40,000 soldiers, family members, and civilian employees working and/or living there.
The Depository, on the other hand — i.e., the place where the bullion reserves are held — is a two-story granite, steel, and poured concrete structure located next to the base. It has a large vault located in its one-story basement. The Depository is controlled by the U.S. Mint, which is part of the U.S. Department of the Treasury. The land was transferred nearly 90 years ago from the U.S. military to the Treasury (in 1935) to construct a secure inland site to house the U.S.’s gold reserves.
Not all that much is known about the vault itself because the U.S. Mint likes to keep that information close to the vest. (Wouldn’t you?) However, its security is said to have been upgraded throughout the years, and the building is rumored to be able to withstand bombs, drilling, and other attacks. Heck, the door of the vault alone reportedly weighs 20 tons!
It’s a Classified Facility, So Access Is Highly Restricted
Unlike the five other U.S. Mint facilities, no one (aside from select authorized individuals) is allowed inside the Fort Knox Depository. There have only been three known exemptions in the facility’s nearly 90-year history, and only one of those occasions included members of the public:
- 1943: Franklin D. Roosevelt is said to have visited Fort Knox and the Depository during his presidency.
- 1974: A congressional delegation and members of the press visited in 1974 to dispel rumors that the vault was empty/didn’t contain gold.
- 2017: Congressional representatives, along with Treasury Secretary Steve Mnuchin and Kentucky Governor Matt Bevin, visited the vaults.
While the U.S. military isn’t in charge of the Fort Knox Bullion Depository, you can bet your bottom dollar that if you tried to break into the Depository, you’d soon find yourself on the wrong end of thousands of rifles, tank gun barrels, and attack helicopters’ machine guns from the neighboring base. So, it’s probably best to avoid that scenario, am I right?
Unfortunately, enterprises don’t have that level of security, which leaves them vulnerable to cybercriminal activities. With this in mind, let’s briefly turn our attention to enterprise cybersecurity to see what lessons we can draw from the classified site and explore one of the primary tools at your disposal to protect your data and other sensitive systems and digital assets.
Part of the discussion will include key aspects of public key infrastructure (PKI). To learn more about what PKI is, you can jump to that section later in the article by clicking on the previous link.
An Overview of What Enterprise Cybersecurity & Security Entail
A term like “enterprise cybersecurity” describes the people, technologies, processes, and procedures that keep your organization’s IT environments, networks, devices, and data secure. It’s a mix of physical and digital security considerations. For example:
- Identity management and access controls
- Physical and cyber attack prevention technologies, tactics, and policies
- Incident detection, identification, analysis, and response tools and procedures
- Damage control and mitigation strategies
- Education and training for your employees, contractors, and other network users
- Business continuity and disaster recovery planning and exercises
Knowing this, it’s now time to dive in and explore some of these areas using Fort Knox as the measure for setting the bar regarding security.
3 Ways to Model Your Enterprise Cybersecurity After Fort Knox
Three core concepts at the heart of Fort Knox’s security correspond well with the aforementioned enterprise security-related considerations:
1. Employ Comprehensive Physical Security
Fort Knox’s Bullion Depository has a wide range of known physical security measures ranging from electric fences and impenetrable layers of steel and concrete to alarm and monitoring systems and access controls. In addition to the U.S. Mint Police, there’s the literal multi-branch military installation next door we mentioned earlier that can step in to help protect it.
Of course, there are plenty of rumors about Fort Knox Bullion Depository’s physical security measures, such as:
- Ground-penetrating radar
- Water-filling vaults
- Laser-triggered machine guns
- On-site armed police
- Unmanned aerial vehicles (UAVs)
- Landmines
- Intrusion detection systems, sensors and monitors
How to Harden Your Enterprise’s Physical Security
As an enterprise, I can pretty much guarantee you don’t have an army or machine guns at your disposal. However, there are steps you can take to make your enterprise cybersecurity as robust as possible:
- Lock down access to your building and/or office
- Restrict access to your server room and devices using physical locks and server enclosures
- Store your secrets (e.g., cryptographic keys, passwords, API tokens, etc.) in offline and online physical hardware security modules (HSMs) depending on the use case
- Require dual access and separation of duties to ensure no one person has physical access to everything or knows all security factors and access procedures
- Install security cameras to monitor and keep a record of physical access
- Install and monitor alarms and sensors (e.g., motion, volumetric or infrared) for additional security
2. Employ a Multi-Layered Approach to Digital and Cyber Security
Not much is publicly known or confirmed about the Fort Knox Bullion Depository’s digital security measures — for good reason. However, something we do know is the U.S. Department of the Treasury has its own Cyber Security Program. It builds on the Federal Information Security Management Act of 2022 (FISMA) and implements additional requirements from various U.S. authorities and other cybersecurity frameworks, including:
- Committee on National Security Systems (CNSS)
- National Institute of Standard and Technology (NIST)
- Office of the Director of National Intelligence (ODNI)
- Office of Management and Budget (OMB)
Considering that the U.S. Mint falls under the Treasury, it likely relies on many of these same digital security and cybersecurity frameworks. So, we can venture a guess that there are certain cybersecurity requirements they must meet. Knowing this, let’s explore some common cybersecurity digital defense measures enterprises and governments employ.
How to Harden Your Enterprise’s Cybersecurity and Digital Defenses
Much like how Fort Knox’s physical perimeter is highly secure, you also want to ensure the same for your digital environment. This involves the use of robust intrusion detection and prevention systems (IDS/IPS). Some examples of the digital security measures you can implement to improve your enterprise’s cybersecurity defenses include:
- Multiple software- and hardware-based firewalls to protect your networks and endpoint devices with multi-layered security
- Up-to-date antivirus and anti-malware scanning tools
- End-to-end encryption that protects data at rest and in transit
- Adopt PKI-based digital identity for secure authentication
- Stringent access controls and password security policies to prevent unauthorized access
- Addi layered digital authentication measures such as multi-factor authentication (MFA)
Ensuring your enterprise’s physical and cyber security requires a multi-layered approach to bridge gaps in your defenses. Physical and digital security measures often go hand in hand and, unsurprisingly, share some overlap with the next core area.
3. Restrict Access to Allow Only Authorized, Authenticated Individuals
Much like the physical and digital security measures, protecting access to your most sensitive resources also requires a stringent, multi-layered approach. This concept is crucial to strong enterprise security and cybersecurity.
Restrict Access to Only Those Who Need It
The principle of least privilege (PoLP) is a crucial part of your enterprise’s physical and cyber defenses. This concept requires organizations to only assign access privileges to users who need access to do their jobs. Authorization plays a critical role, as it involves intentionally assigning specific permissions to each individual or group.
We’ve discussed robust access controls many times in our articles. The same story rings true whether you’re an enterprise or one of the U.S. government’s most heavily guarded facilities: only give access to individuals whose jobs or roles require it.
It doesn’t matter who’s asking — if someone isn’t on your list of approved, authorized users, then they shouldn’t have access to your servers, data, or other sensitive resources. Heck, the Fort Knox Bullion Depository has turned away former presidents, keeping them from visiting the classified site. So, if they can say no to the country’s Commanders in Chief, surely you can say no to Mary in Marketing.
Use Verifiable Means of Authentication
It’s not enough to simply have names on a list; employees or other network users must prove that they are who they claim to be. Access to your organization’s most sensitive resources and data must be strictly limited to authorized, authenticated individuals.
Cybercriminals and even disgruntled network users can claim to be virtually anyone. For example, I could claim to be the actress Natalie Portman, but that doesn’t make it true. Put the onus on the individual to prove their identity by providing verifiable authentication data.
One way to help employees prove their identities is to use physical access ID cards. To prove their digital identities, you can also have PKI-based user authentication, which enables users to prove their identities without having to remember any tricky or hard-to-recall passwords. This passwordless approach helps to prevent bad guys from brute-forcing their way into an authorized user’s account because they won’t have access to the authentication certificate or key.
Implement Dual Authorization as a Minimum
Fort Knox requires multiple repository staff members to have key pieces of information to access critical systems or the vault itself. This distribution of knowledge factors (e.g., lock number combinations and procedures) and physical access methods (e.g., keys, tokens, access cards, etc.) ensures no one person can access the vault independently.
Likewise, your organization should also have security measures and access controls in place to secure everything from your website and database APIs to your private PKI root of trust. For example, it should require two people as a minimum to access the secure space where your private CA root server and HSM-secured keys are stored.
Revoke Access Once It’s No Longer Required
Just as how you don’t want to grant access permissions or privileges to someone who doesn’t need them, you also want to pull access for individuals who have it but no longer need it to do their jobs.
In the military, when a soldier PCSes or ETSes (i.e., is either reassigned to a new duty station or reaches the end of their contract), they must turn in their access cards, keys, and other forms of access. Likewise, for enterprises, when an employee changes jobs, gets reassigned, quits, or otherwise leaves the company, their access must also be revoked, and accounts deactivated.
Every additional person with access privileges to sensitive systems represents a potential attack surface or door to your network. Don’t give attackers a chance to gain access through an account or ID card that should have been deactivated. Have the policies and procedures in place to deal with these things before they become liabilities.
PKI Is at the Heart of Enterprise Cybersecurity
Data is your gold bullion; it’s among your company’s most valuable assets. And just as Fort Knox’s security measures protect part of the nation’s precious metal stores, you also need to use the most trusted and reliable security and authentication methods to protect your data.
Public key infrastructure can help you do this. PKI is the underlying foundation of security for public and private network resources. So long as it’s properly configured and managed, it enables users to securely exchange data remotely using authenticated connections and provides assurance that data, files, and communications are legitimate. This enhances your enterprise security and cybersecurity immensely.
Enterprises generally take a two-pronged approach, using both public and private CAs:
- Public PKI certificates to secure websites, software apps, web apps, documents, emails, and other public-facing resources, and
- Private PKI to secure valuable internal resources, such as intranet sites, internal software, users, and smart devices.
Authentication Makes Trust in an Insecure Digital World
With public and private PKI, securely exchanging data no longer means clandestine face-to-face meetings that used to be required. Instead, you can send emails, download software, receive data from your IoT devices, and make online purchases without having to worry about bad guys reading, stealing, or manipulating your data in transit. This is because the data is sent via encrypted, authenticated connections.
You can verify who or what is on the other end of that encrypted connection and rest assured that your data has been transmitted securely to your intended recipient.
PKI Contributes to a Zero-Trust Architecture
Several years ago, the U.S. Mint began its transition to a zero-trust architecture as part of its response to the White House’s Memorandum on Improving the Cybersecurity of National Security, Department of Defense, and Intelligence Community Systems. The idea here is that no one is trusted automatically, and everyone (users inside and outside your network alike) must be continually authenticated.
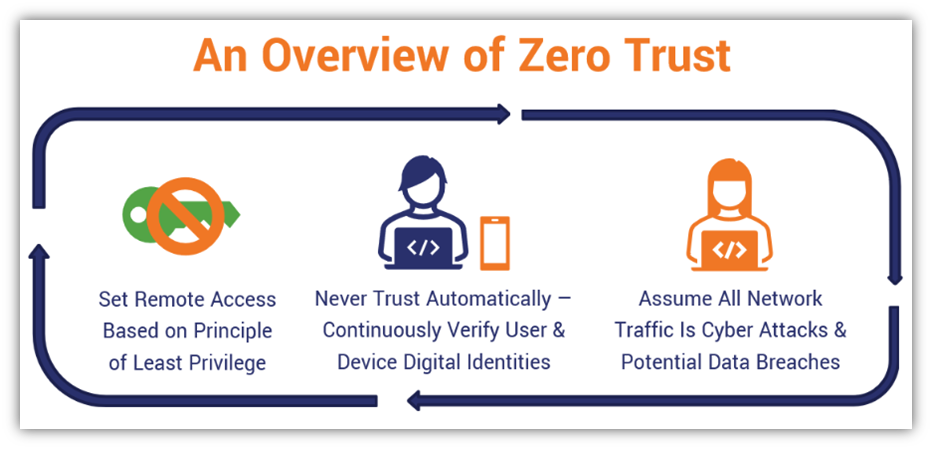
PKI-based authentication enables users to securely access authorized resources while providing assurance that they’re legitimate account holders and not imposters.
PKI Secures Your Internal and External Server Connections
Robust enterprise security extends beyond preventing access to your invaluable material. It’s also about ensuring that if bad guys do manage to get their paws on your encrypted data, they can’t do anything with it.
When you encrypt your data transmissions for emails, websites, and other digital communications, it’s protected using public key cryptography. This means that unless a bad guy has access to the private key, they can’t do anything with the data because all they’ll see is gibberish.
We’ve spoken many times about the importance of using SSL/TLS encryption to protect the connections of your public-facing websites, web apps, and other digital resources. (Adding this extra layer of encryption makes the “https” appear in users’ browsers.) However, it’s equally important to use the SSL/TLS protocol to protect your internal systems and communications as well.
You can use private SSL/TLS certificates to secure your internal websites, web apps, and API connections. These certificates are issued by a private CA that you own and/or operate.
Centralize Your PKI Security Monitoring and Management Systems
Keeping a close eye on your company’s IT environment is easier when you take a centralized approach. The same can be said about your private PKI for strong enterprise security.
Tracking all of your digital certificates in a single pane of glass simplifies your certificate lifecycle management responsibilities. When all of your PKI lifecycle management-related tools are integrated into a single solution, you don’t have to worry about third-party vendor service disruptions or the inevitable vulnerabilities that’ll have to be patched on their ends that leave your system vulnerable.
DigiCert Trust Lifecycle Manager is a full-stack digital trust solution. It allows you to track and manage all of the certificates within your digital environment, regardless of which certificate authority (CA) issued them. Another benefit is that it helps improve your crypto agility by allowing you to incorporate post-quantum cryptographic algorithms into your architecture.
DigiCert Trust Lifecycle Manager Simplifies PKI & Digital Certificate Management
DigiCert Trust Lifecycle Manager is an all-in-one certificate lifecycle management (CLM) solution. Explore how this tool can help you keep a close eye on your PKI and avoid certificate outages.
PKI is at the heart of enterprise cybersecurity. Reach out to our Sales team to learn more about how DigiCert Trust Lifecycle Manager can help your organization become a digitally secure fortress.


























































Be the first to comment